
Private data, especially when it comes to cryptocurrency, is too valuable to leave unprotected. With cybercriminals developing increasingly sophisticated hacking methods, the security of crypto private keys has become an increasing concern for investors.
The iPhone offers features that could potentially secure these private keys. But the question is, how safe are these methods?
Hidden Features on iPhones to Store Crypto Private Keys
Apple’s iPhones, renowned for their robust security mechanisms, do not natively have a “Secure Folder” functionality like some Android devices. However, alternative means to secure private data have emerged from Apple’s offerings and third-party applications.
For instance, the iOS 16 update in September 2022 introduced the option to unlock the “Hidden Album” within the Photos app using a passcode, Touch ID, or Face ID. This significantly enhances the app’s privacy, which previously allowed anyone access to the hidden contents through the Albums function.
While the primary intent of the app is for photos and videos, this function could help secure crypto private key screenshots.
Additionally, the Notes app on the iPhone presents an option to lock individual notes containing text, images, and videos behind a password. This feature could also be leveraged to store encrypted crypto private key versions securely.
Apple’s Third-Party Apps Can Also Help Secure Data
A range of third-party apps further extends the iPhone’s ability to secure data. For instance, OneDrive’s Personal Vault provides an additional layer of security. It requires extra authentication to access the data within the vault.
Other apps like Folder Lock, Best Secret Folder, and MaxVault offer password-protected places to safeguard sensitive files and documents, including images of encrypted crypto private keys.
However, the security question goes beyond merely securing the private keys within an app. As the world moves into the era of cloud storage, another point of contention arises: Is it safe to store private crypto keys in the cloud?
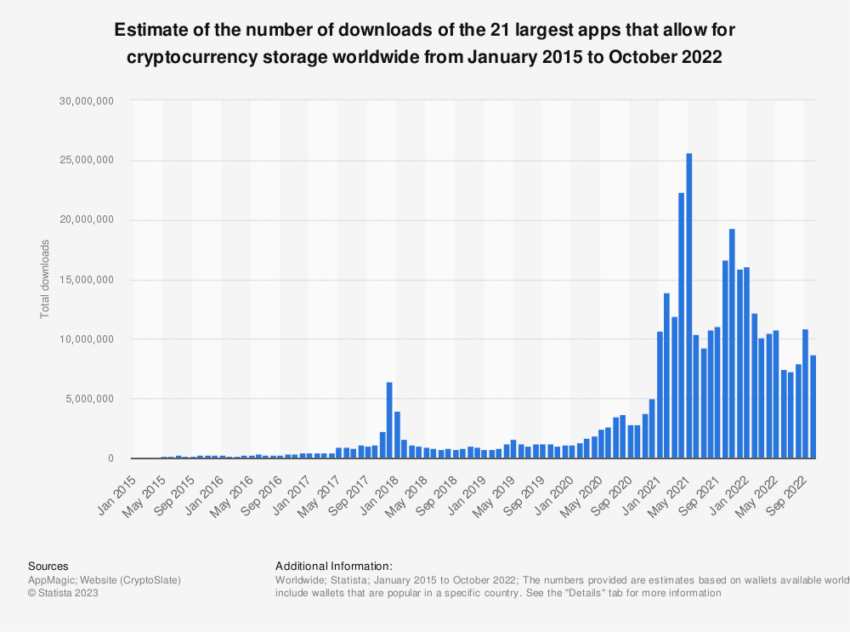
This question was brought to the fore when Coinbase, a leading crypto exchange, announced that users could back up an encrypted version of their private keys on Google Drive or iCloud. While this option safeguards against losing devices or misplaced keys, it also carries inherent security risks.
Cloud storage providers represent centralized hubs that could potentially experience security breaches, leaving encrypted keys vulnerable to cybercriminals. Furthermore, there is the persistent threat of phishing scams, where users can be tricked into revealing their credentials to counterfeit websites.
Even though iCloud, for instance, offers state-of-the-art security, storing private keys in the cloud is not without risks. The lure of convenience may not outweigh the potential threat to cryptocurrencies.
Safest Way to Store Crypto Private Keys
While iPhones offer a suite of features and applications to secure crypto private keys, weighing the convenience against the security risks is imperative. The responsibility of safeguarding crypto assets ultimately falls on the individual holder, who must remain vigilant.
Arguably, hardware wallets represent the safest way to store crypto. They are physical devices that store the private keys to cryptocurrency addresses offline. Subsequently rendering them immune to hacking attempts.
However, the effectiveness of this cold storage method depends on careful usage, including secure device handling, strong passphrase creation, and regular firmware updates. Private keys should not be shared with others or stored online or on a computer.
Although some perceive cold storage devices as cumbersome, they only introduce an extra step – plugging into a computer. Therefore, a dual-layer strategy to manage risks while simplifying wallet and private key management can be the answer.
Hot Wallet Layer: Hot wallets are online-ready, facilitating faster interaction with online services. This is the wallet address provided to exchanges when withdrawing or depositing or using decentralized applications (dApps).
Cold Storage Layer: After interacting with online protocols or if crypto is intended for long-term holding, transferring them to a cold wallet is advisable.
In addition to these digital measures, it is important to maintain a physical record of private keys and recovery phrases. This record should be stored offline and securely on paper or a metal engraving in a safe.
Disclaimer
Following the Trust Project guidelines, this feature article presents opinions and perspectives from industry experts or individuals. BeInCrypto is dedicated to transparent reporting, but the views expressed in this article do not necessarily reflect those of BeInCrypto or its staff. Readers should verify information independently and consult with a professional before making decisions based on this content.




Be the first to comment